The cyberthieves who stole millions of credit and debit card numbers from major U.S. retailers and restaurant chains in recent years have been caught.
U.S. law enforcement authorities announced Wednesday the arrests and indictment of three leaders of FIN7, a notorious Eastern European cybercriminal group long suspected of carrying out several waves of attacks on more than 120 U.S. companies between 2015 and 2017.
The targeted companies were predominantly in the restaurant, gaming and hospitality industries, with prosecutors disclosing the names of only even, including Chipotle Mexican Grill, Chili’s, Arby’s, Red Robin and Jason’s Deli, all of which have publicly attributed recent data breaches to FIN7.
Three hackers
Officials identified the three arrested FIN7 leaders as Ukrainian nationals Dmytro Fedorov, 44, Fedir Hladyr, 33,and Andrii Kolpakov, 30.
Hladyr, the group’s alleged systems administrator, is in federal custody in Seattle after being arrested in Germany in January and extradited to the United States in early May.
Fedorov, who allegedly supervised other FIN7 hackers, and Kolpakov, another purported supervisor for the group, remain in custody in Poland and Spain respectively pending their extradition to the United States.
The three hackers were each charged in federal court in Seattle on Wednesday with 26 counts of conspiracy, wire fraud, computer hacking, access device fraud, and aggravated identity theft.
“The naming of these FIN7 leaders marks a major step towards dismantling this sophisticated criminal enterprise,” Special Agent in Charge Jay S. Tabb Jr. of the FBI’s Seattle field office said at a press conference in Seattle.
Cybercrime is a $600 billion global business, according to Dan Short, a senior director at Visa. The crooks and scam artists that inhabit the ecosystem have grown increasingly sophisticated in recent years, making their capture more difficult.
Public-private cooperation
But growing cooperation among private companies, cybersecurity firms, and law enforcement agencies has led to a string of high profile takedowns of cybercriminal enterprises over the past year.
Richard Downing, an acting deputy assistant attorney general, said law enforcement authorities would not have caught the three hackers “if it weren’t for our relationships with law enforcement agencies in other countries.”
Credit card giants Visa and Mastercard, both victims of massive data breaches in recent years, said they cooperated with the FIN7 investigation, which is still ongoing.
Kimberly Goody, manager of financial crime analysis at FireEye, a leading cybersecurity firm that works with law enforcement, said the FIN7 arrests demonstrated the impact of public-private partnerships in cybercriminal investigations.
“As sophisticated threat groups like FIN7 continue to emerge, partnerships between governments, private industry, and cybersecurity companies will play a very important role in combating these threats,” she said.
Prolific hacking group
Goody said FIN7’s “exceptional social engineering savvy and innovative methods to evade detection played a key role in their rise as a sophisticated organized criminal enterprise.”
Law enforcement officials describedFIN7 as “a prolific hacking group” composed of dozens of hackers that developed various malware and operated servers in several countries, including the United States.
To operate under the guise of a legitimate business, FIN7 created a computer security pen testing company called Combi Security, purportedly with offices in Russia and Israel.
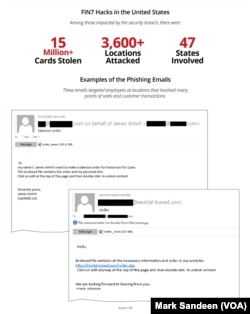
To gain access to the computer networks of the businesses, FIN7 hackers used a technique knowing as phishing, emailing their employees well-crafted, legitimate-looking messages with attachments embedded with malware. The employees would be urged to open the attachments to read details of their purported catering or hotel reservation orders. Once opened, the malware would be activated, allowing the hackers access to the company’s computer networks.
According to the indictment, FIN7 frequently targeted companies whose customers use credit and debit cards when they make a purchase at so-called point-of-sale systems.
15 million card numbers
The indictment says that FIN7 stole more than 15 million payment card numbers from more than 6,500 point-of-sale terminals at more than 3,600 business locations in 47 states and the District of Columbia.
The attackers also targeted companies in England, Australia and France.
The stolen data was then offered for sale on criminal marketplaces on the internet and websites such as Joker’s Stash.
Annette Hayes, U.S. Attorney for Western Washington State, where some of the victim companies are based, said the loss from the stolen cards is in the tens of millions of dollars.
“Cybercriminals who believe that they can hide in faraway countries and operate behind keyboards without getting caught are just plain wrong,” Hayes said.